| |

linking INTEGRITY
Integrity - use of values or principles to guide action in the situation at hand. Below are links and discussion related to the values of freedom, hope, trust, privacy, responsibility, safety, and well-being, within business and government situations arising in the areas of security, privacy, technology, corporate governance, sustainability, and CSR.
Security Starter Kit - Protection First, 25.4.06
Download.comby Jason Parker (4/27/06) Viruses, spyware, and hackers--oh my! These days, it seems as soon as we connect our computers to the Internet, a whole gang of bad guys is waiting to infiltrate our systems and steal our personal information. To help you set up your computer with a basic security system, we've put together some must-have programs that will act like a fortified castle for your PC.
Whether you have a new machine or simply want to bolster the security on your old one, take a look at our list of safety categories to see which areas you have covered. If there are holes in your defense, download one of our suggestions or look at our software library in your particular area of need. If you have security suggestions for Download.com users, please add them to our Security Discussions.
One thing to always remember is that while these free or cheap programs are all high quality, no system is 100 percent safe. That caveat aside, these programs will lower the chances of an attack considerably. Also, ignoring any of these security categories can be extremely dangerous to your data and personal information.
[Read further to establish good security as soon as you contect to the Internet.]
(0) comments
RFID DOS attacks, 14.4.06
SCISSEC - Security Research Group RFID Vulnerabilities Uncovered in new UHF tags - Update RFID Vulnerabilities Uncovered in new UHF tags - Update
The research efforts of the SCISSEC group have uncovered, documented and tested a range of attacks on the newer UHF RFID tags.
Vulnerabilities in the newer UHF style of RFID tags have been found and are of concern for anyone trying to implement a RFID system that would have mission critical or human life issues involved in it.
[read more]
[research more]
(0) comments
McAfee Threat Center, 12.4.06
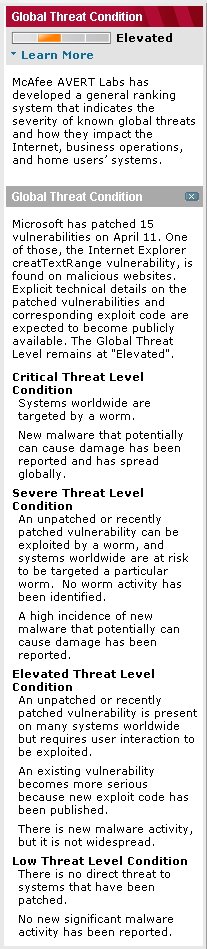 McAfee Threat Center McAfee Threat Center
 AVERT® Labs helps you maintain the highest possible level of security. 100 researchers in 14 countries continuously monitor the latest threats and provide remediation, so that you can stay ahead of the latest threats and respond quickly to emergencies. AVERT® Labs helps you maintain the highest possible level of security. 100 researchers in 14 countries continuously monitor the latest threats and provide remediation, so that you can stay ahead of the latest threats and respond quickly to emergencies.
The threat dashboard list the latest:
Top Malware
Current Vulnerabilities
Top Potentially Unwanted Programs
Latest Spam Activity
Top Phish Scams
Live Hacker Activity Map
Global Threat Condition (sample to the right)
Top 10 Spam Subject Lines:
Listed below are ten of the most common spam subject lines received from customers within the last 24 hours.
Spam campaigns can change rapidly so any spam, or missed spam, you receive in your inbox may not necessarily correspond with the spam subjects in this list, as these subjects may be blocked by your Anti-Spam software if installed.
1. today news
2. great deals on new cars
3. hi
4. Sorry
5. News from DLsoft 100% instant rebate invitation only
6. your home
7. good info
8. software
9. Hi
10. Premier
(0) comments
Emergency and Information Service, 5.4.06
RSOE HAVARIADisaster events in the last 24 hours on a real time world map. I.e. Major accidents: (Plains, Trains & Ferries etc), Disease Outbreaks (Bird flu & Cholera etc), Earthquakes WX events and related evacuations.
  
(0) comments
Corporate Reputation: Connecting Fantasies with Reality,
Ipsos How can corporations increase the concordance between their projected image and the real one, thus strengthening the corporation’s credibility at a time when brands suffer from a legitimacy crisis? Ipsos measures corporations’ reputation and image among their stakeholders: shareholders, consumer-clients,media, and employees. How can corporations increase the concordance between their projected image and the real one, thus strengthening the corporation’s credibility at a time when brands suffer from a legitimacy crisis? Ipsos measures corporations’ reputation and image among their stakeholders: shareholders, consumer-clients,media, and employees.
Download the complete issue in English, French or Spanish
(0) comments
ISM3, 3.4.06
ISM3, a standard for advanced information security management
The Information Security Management Maturity Model (ISM3, or ISM-cubed) offers a practical and efficient approach for specifying, implementing and evaluating process-oriented information security management (ISM) systems.
ISM3 aims to:
- Enable the creation of ISM systems that are fully aligned with the business mission.
- Be applicable to any organization regardless of size, context and resources.
- Enable organisations to prioritize and optimize their investment in information security.
- Enable continuous improvement of ISM systems.
- Support the outsourcing of security processes.
ISM3 is compatible with the implementation and use of ITIL, ISO9001, Cobit and ISO27001. This compatibility protects the existing investment in ISM systems when they are enhanced using ISM3. ISM3 based ISM systems are themselves accreditable, giving organisations an objective means of measuring and advertising their progress with information security management. The management discipline and internal control framework required by ISM3 assists compliance with corporate governance law.
The significant features of ISM3 are
Metrics for Information Security - “What you can't measure, you can't manage, and what you can't manage, you can't improve” - ISM3 v1.20 makes information security a “measurable” process by using metrics for every process, making it probably the first information security standard to do so. This allows for a continuous improvement of the processes, as there are criterion to measure the efficiency and performance of the informations security management system.
Maturity Levels - With this standard it is possible to create ISMS (Information Security Management Systems) for small and big organizations. ISM3 has 5 maturity levels, each level tailored to the security objectives of the organization and available resources. This makes it a standard for small organizations to behemoths.
Process Based - ISM3 v1.20 is process based, which makes it specially attractive for organizations familiar with ISO9001 or those that use ITIL for as the IT management model. Using ISM3 fosters the collaboration between information security clients and providers, as the outsourcing of security processes is enable by explicit mechanisms for outsourcing.
Adopts best practices - ISM3 implementation enjoys of advantages like the extensive reference to established standards for every process, and the explicit distribution of responsibilities in the organization between leaders, managers and technical personnel using the concept of “Strategic, Tactical and Operational Management” for Information Security.
Accreditation - ISMS based in ISM3 are Accreditable under ISO9001 or ISO27001 schemes, which means that you can use ISM3 to implement an ISO 27001 based ISMS. This will be attractive as well to organizations that are already quality certified and have experience and infrastructure for ISO9001.
Business Friendly - A key advantage of using ISM3 for ISMS is that Senior Managers and Stake Holders are able to clearly see Information Security as a business investment and measure ROSI ( Return on Security Investment).
(0) comments
|
|
Integrity Incorporated
Site Feed
|
"We shall need compromises in the days ahead, to be sure. But these will be, or should be, compromises of issues, not
principles. We can compromise our political positions, but not ourselves. We can resolve the clash of interests without
conceding our ideals. And even the necessity for the right kind of compromise does not eliminate the need for those
idealists and reformers who keep our compromises moving ahead, who prevent all political situations from meeting the
description supplied by Shaw: "smirched with compromise, rotted with opportunism, mildewed by expedience, stretched out
of shape with wirepulling and putrefied with permeation.
Compromise need not mean cowardice. .."
John Fitzgerald Kennedy, "Profiles in Courage"
|
Archives
07.03
08.03
09.03
10.03
11.03
12.03
01.04
02.04
03.04
04.04
05.04
06.04
07.04
08.04
09.04
10.04
11.04
12.04
01.05
02.05
03.05
04.05
05.05
06.05
07.05
08.05
09.05
10.05
11.05
12.05
01.06
02.06
03.06
04.06
05.06
06.06
08.06
09.06
10.06
11.06
01.07
02.07
03.07
04.07
07.07
08.07
09.07
10.07
05.08
06.08
| |
